The last few weeks of the year are usually the best to start testing systems at my current job. We currently have the following security measures in place:
Cisco Firewalls
Juniper Firewalls
Cisco IPS
Cisco Switches with ACLs on each VLAN
Secured Syslog Server
Secured Snort (IDS) Server
McAfee Antivirus
Windows Updates*
*Windows Updates are not forced on the Dev Team or Server Farms – Those updates are installed manually usually once a quarter (after testing).
Seeing as it’s Tuesday December 28th, I had some free time to test out the Antivirus installed on each system. Most exploits today are not actually against the OS (Microsoft has done a pretty decent job lately with security issues, even with that huge DLL issue) and are instead targeting 3rd party applications.
What do you consider a 3rd party application? The biggest two are:
Adobe (PDF Reader, Flash Player)
Sun (Java)
So I decided to test in my VMWare environment using the latest and greatest updates for Windows XP. Why did I choose XP over 7? Looking over my log files I see that most visitors to my site include XP users. XP has also been around long enough to get all the kinks worked out. And finally, I chose to use PDF/Java exploits, so the OS doesn’t really matter as much.
Please don’t visit these websites unless you know what you’re doing. And I used smartscan/quickscan whenever possible.
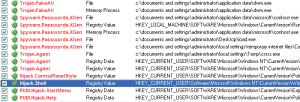
Test 1 (Nod32/Threatfire):
Windows XP Pro SP3
Fully Updated 12.28.2010
Internet Explorer 8.0.6001.18702
Nod32 Antivirus 4.2.67.10 5739
Threatfire 4.7.0.17
Secunia PSI 2.0.0.1002 100%
Adobe Flash Player 10 ActiveX 10.1.102.64
Java 6 Update 23 6.0.230
Malwarebytes Anti-Malware 1.50.1.1100 5408cryyahoo.info/tre/boba.exe
Blocked by Nod – Downloaded Java (c:\doc and set\Administratorupdate665744669.exe) **PDF/Java/Trojan**expa82.co.cc/bl2/
Blocked by Nod **Trojan**1.oresmir.co.cc/1/load.php?spl=mdac
IE labeled download as unsafe, Cleaned by Nod **Trojan**marinada3.com/77/throatnut.php
Blocked by IE – Java exploit blocked by Nod (Freezes IE) **Java/Trojan**Malwarebytes:
Objects infected: 3 (3 are non-infection related)Verdict:
Clean system, difficult to infect on accident.
Performed scan by Nod32/Threatfire – nothing found.
Test 2 (McAfee):
Windows XP Pro SP3
Fully Updated 12.28.2010
Internet Explorer 8.0.6001.18702
McAfee VirusScan Enterprise 8.7i 6210.0000
Adobe Flash Player 10 ActiveX 10.1.102.64
Java 6 Update 23 6.0.230
Malwarebytes Anti-Malware 1.50.1.1100 5408cryyahoo.info/tre/boba.exe
Allowed to download – no extra processesexpa82.co.cc/bl2/
Allowed to load page – no extra processes1.oresmir.co.cc/1/load.php?spl=mdac
IE labeled download as unsafe, allowed to install (load.exe, csrss in temp folder)marinada3.com/77/throatnut.php
Blocked by IE – no extra processesMalwarebytes:
Objects infected: 14 (3 are non-infection related)Verdict:
CSRSS.EXE running as SYSTEM and Administrator. Infected system.
Performed scan by McAfee – nothing found.
Test 3 (McAfee/Threatfire):
Windows XP Pro SP3
Fully Updated 12.28.2010
Internet Explorer 8.0.6001.18702
McAfee VirusScan Enterprise 8.7i 6210.0000
Threatfire 4.7.0.17
Adobe Flash Player 10 ActiveX 10.1.102.64
Java 6 Update 23 6.0.230
Malwarebytes Anti-Malware 1.50.1.1100 5408cryyahoo.info/tre/boba.exe
Allowed to load page – file would not downloadexpa82.co.cc/bl2/
Allowed to load page – no extra processes1.oresmir.co.cc/1/load.php?spl=mdac
IE labeled download as unsafe, Threatfire detected and blocked the installation, then found and blocked load.exemarinada3.com/77/throatnut.php
Blocked by IE – no extra processesMalwarebytes:
Objects infected: 4 (3 are non-infection related)Verdict:
Only infection file was located as a temporary internet file download and was not referenced in the registry. “Clean” system.
Performed scan by McAfee and Threatfire – nothing found.
Test 4 (Nod32):
Windows XP Pro SP3
Fully Updated 12.28.2010
Internet Explorer 8.0.6001.18702
Nod32 Antivirus 4.2.67.10 5739
Adobe Flash Player 10 ActiveX 10.1.102.64
Java 6 Update 23 6.0.230
Malwarebytes Anti-Malware 1.50.1.1100 5408cryyahoo.info/tre/boba.exe
Blocked by Nodexpa82.co.cc/bl2/
Blocked by Nod1.oresmir.co.cc/1/load.php?spl=mdac
IE labeled download as unsafe – Not found by Nod32marinada3.com/77/throatnut.php
Blocked by IE – Java exploit blocked by Nod32Malwarebytes:
Objects infected: 13 (3 are non-infection related)Verdict:
Infected system, somewhat hard to infect on accident, but a definite possibility. CSRSS.exe is loading.
Performed scan by Nod32 – nothing found.
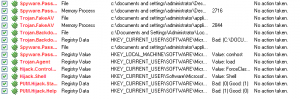
Test 5 (No AV):
Windows XP Pro SP3
Fully Updated 12.28.2010
Internet Explorer 8.0.6001.18702
Adobe Flash Player 10 ActiveX 10.1.102.64
Java 6 Update 23 6.0.230
Malwarebytes Anti-Malware 1.50.1.1100 5408cryyahoo.info/tre/boba.exe
IE reported this site as BAD – File not found to downloadexpa82.co.cc/bl2/
Site loaded fine – no extra processes1.oresmir.co.cc/1/load.php?spl=mdac
IE labeled download as unsafe – Saved and run successfullymarinada3.com/77/throatnut.php
Blocked by IE – Java exploit allowed to load – no additional processesMalwarebytes: (google searches redirected to other websites, had to kill load.exe)
Objects infected: 14 (3 are non-infection related)Verdict:
It’s always better to have some sort of antivirus software installed. So I can’t recommend this at all.

Test 6 (Microsoft Security Essentials MSE):
Windows XP Pro SP3
Fully Updated 12.28.2010
Internet Explorer 8.0.6001.18702
Adobe Flash Player 10 ActiveX 10.1.102.64
Java 6 Update 23 6.0.230
Malwarebytes Anti-Malware 1.50.1.1100 5408cryyahoo.info/tre/boba.exe
IE reported this site as BAD – File not found to downloadexpa82.co.cc/bl2/
Site loaded fine – no extra processes1.oresmir.co.cc/1/load.php?spl=mdac
IE labeled download as unsafe – Saved and run successfullymarinada3.com/77/throatnut.php
Blocked by IE – Java exploit allowed to load – no additional processesMSE found a few files it needed to send in for verification, but did not block anything.
Malwarebytes:
Objects infected: 12 (3 are non-infection related)Verdict:
MSE didn’t actively block anything – it only found the files when I scanned the computer using MSE. I prefer a more active participant.

Test 7 (Microsoft Security Essentials MSE with TF):
Windows XP Pro SP3
Fully Updated 12.28.2010
Internet Explorer 8.0.6001.18702
Adobe Flash Player 10 ActiveX 10.1.102.64
Java 6 Update 23 6.0.230
Malwarebytes Anti-Malware 1.50.1.1100 5408
Threatfire 4.7.0.17cryyahoo.info/tre/boba.exe
IE reported this site as BAD – File not found to downloadexpa82.co.cc/bl2/
Site loaded fine – no extra processes1.oresmir.co.cc/1/load.php?spl=mdac
IE labeled download as unsafe – Threatfire blocked the installationmarinada3.com/77/throatnut.php
Blocked by IE – Threatfire blocked the java exploit from runningMSE, like in the previous test, did not block anything.
Malwarebytes:
Objects infected: 3 (3 are non-infection related)Verdict:
MSE didn’t actively block anything – it only worked well with TF in finding new problem programs. I still prefer a more active participant, but MSE and TF worked well.

Final Results:
So it appears as though Threatfire really does help out. It also appears that Nod32 is only slightly better than McAfee and MSE edged them both out. McAfee did not find the infections on access or during a scan. Nod32 blocked only one file on access, but found nothing during a scan. MSE blocked nothing during on access, but found a couple files with issues during a scan.
I also realize that I didn’t include Adobe Reader as part of the package. Since I’ve already disposed of the virtual machines I don’t think I’ll go back and correct this error.
No AV – 11 infections
McAfee – 11 infections
Nod32 – 10 infections
MSE – 9 infections
McAfee with Threatfire – 1 infection
Nod32 with Threatfire – 0 infections
MSE with Threatfire – 0 infections
Final recommendation:
While I will continue to use Nod32 alongside Threatfire (I pay for the Nod32 subscription), and will continue to recommend it to my peers/clients, I must say that for the average home user MSE has come through with flying colors. However, when utilizing MSE you MUST scan your system after each download or on regular scanning intervals. Their lack of on-access scanning is my major gripe at this time.