I’m going to try to make this as easy to understand as possible so bear with me. It’s a very geeky topic and I’m not usually a great writer, so I’ll try to not make it incredibly boring. Or long. Well, it’ll probably be long, but it should be a decent read.
OSI Model
First we have to at least look at the OSI (Open System Interconnection) model. You don’t have to completely understand it, but a few reference points would be mighty handy.
There are 7 layers to the OSI model:
1.) Physical Layer – The actual physical connection (modem cable, serial cable, ethernet cable, etc)
2.) Data Link Layer – Provides the functionality and means to transfer data (MAC Addresses)
3.) Network Layer – IP layer (TCP and UDP)
4.) Transport Layer – Provides reliability controls to the layers above (QoS)
5.) Session Layer – Mechanism for opening and closing sessions
6.) Presentation layer – Encryption layer, also responsible for formatting data for the Application layer
7.) Application Layer – Final layer in which applications (Web browser, Email client) take the formatted data and display it for the user
Keywords
Next I’d like to try out keywords – just to see if you know what is what.
ICMP – Internet Control Message Protocol, or Ping, is used to send error messages regarding host connectivity
Packet – Payload of formatted data sent by network devices
MAC Address – Media Access Control address is a unique physical ID embedded on every network device. It’s a 48bit address of six groups of 2 digits separated by hyphens or colons (01-23-45-67-89-ab)
IP Address – Internet Protocol address is a numbered 32bit address consisting of four groups of 3 digits separated by periods (127.0.0.1 and 192.168.1.1)
Switch – a switch is a device with multiple ethernet ports that connects network devices
Router – Chooses paths for packets and connects different networks together
Ethernet – Patch cable, consists of 8 wires with an RJ45 connector. It’s like a phone cable on drugs.
QoS – Quality of Service. Allows for certain traffic to be flagged at higher priorities than other traffic. Usually Servers beat out clients, and IP Phone conversations beat out web browsing.
Duplex – Full or half duplex. Full duplex means a network connection can send AND receive at the same time at the same speed. Half duplex is a walkie-talkie system in which the system must wait for a free moment to speak.
WAN/LAN – Wide area network/Local area network. WAN refers to an internet/cloud connection, LAN refers to any locally connected devices. WLAN refers to Wireless Local Area Networks.
NAT – Network address translation. Allows for several systems to use the same public IP address at the same time.
Ports – a connection on a switch, hub, or router.
TCP Ports – Ports are added onto TCP/UDP packet headers for destination use. Ports range from 0 to 65535. Port 80 is used for web browsing.
I already know that I will have to write up another one for IPv6 information. This is only for IPv4. IPv4 addresses are said to be exhausted by June 2011.
What is an IP address?
The basic building block of the internet is the IP address. IP addresses (IPv4 anyway) are 4 sets of numbers 0 through 255 separated by a ‘.’ Examples include 4.2.2.2, 192.168.1.1, 172.16.40.254.
There are Class A, Class B, Class C, Class D, and Class E networks (for all of our purposes you only have to remember AB and C).
Class A: 128 available networks each having 16,777,216 IP addresses. Start address is 0.0.0.0 end address is 127.255.255.255
Class B: 16,384 available networks each having 65,536 IP addresses. Start address is 128.0.0.0 end address is 191.255.255.255
Class C: 2,097,152 available networks each having 256 IP addresses. Start address is 192.0.0.0 end address is 223.255.255.255
Class D: Used for multicast on networks, reserved for private use. Start address is 224.0.0.0 end address is 239.255.255.255
Class E: Reserved but not in use. Start address is 240.0.0.0 and end address is 255.255.255.255
Unfortunately not all IP address can be used – there are quite a few that are reserved for private purposes:
0.0.0.0 through 0.255.255.255 is known as the Zero Addresses and cannot be used currently.
10.0.0.0 through 10.255.255.255 is a private IP address scheme for Class A. These are unroutable IP addresses (they only exist in private networks).
127.0.0.0 through 127.255.255.255 is a localhost/loopback address range. 127.0.0.1 is always set as the localhost and can not be routed to the internet.
169.254.0.0 through 169.254.255.255 is for zeroconfig addresses when a DHCP server is not working or present on the network.
172.16.0.0 through 172.31.255.255 is a private IP address scheme for Class B. These are unroutable IP addresses (they only exist in private networks).
192.168.0.0 through 192.168.255.255 is a private IP address scheme for Class C. These are unroutable IP addresses (they only exist in private networks).
224.0.0.0 through 239.255.255.255 is reserved for multicast use. These are unroutable IP addresses.
240.0.0.0 through 255.255.255.255 is reserved and not used in the routing of internet IPs.
What the heck is Netmasking?
Netmasking is a way to differentiate between networks. This is also called subnetting. In the early days of the internet, if a company needed more IP addresses than a Class B network (say 67 thousand IP addresses were “needed”), they’d have to get either 2 class B networks (need 67 thousand, given 131 thousand) or a class A network (need 67 thousand, given 16 million). Now we have a way to lower the number of IPs given out for each class.
You may have seen the netmask 255.255.255.0 before – it’s the most common for home networks. You probably have an IP address of 192.168.1.50 with a netmask of 255.255.255.0. The 255’s mean that the network you are currently on must match. So your network is 192.168.1.0 through 192.168.1.255. If you had a subnet of 255.255.0.0 your network would be 192.168.0.0 through 192.168.255.255. If you had a subnet of 255.0.0.0 your network would be 192.0.0.0 through 192.255.255.255. See how that works?
And yes, you can divide it further – since there are only 2 million available class C networks we can divide them further:
192.168.1.0 with a netmask of 255.255.255.128 would mean that you have the network 192.168.1.0 through 192.168.1.127. If you have 192.168.1.128 with a netmask of 255.255.255.128 that would mean you have 192.168.1.128 through 192.168.1.255. That gives you 128 hosts.
Ah, but we can do better than that. What if you only want 16 hosts? 192.168.1.0 netmask 255.255.255.240. IP range would be 192.168.1.0 through 192.168.1.15. It’d also be a range of 192.168.1.16 through 192.168.1.31. Also 192.168.1.32 through 192.168.1.47. See how that works?
Each of these networks is different. In the last example with the netmask of 255.255.255.240, we see that all of the IP addresses have a 192.168.1.X start. But a computer with an IP of 192.168.1.4/255.255.255.240 could NOT ping a computer with an IP of 192.168.1.18/255.255.255.240 without the use of a router.
What’s so special about routers?
A router, or layer 3 switch, is required to connect different networks. If you were to run a trace route to apple.com, you will see that many routers are necessary for your packet to succeed. Here’s mine:
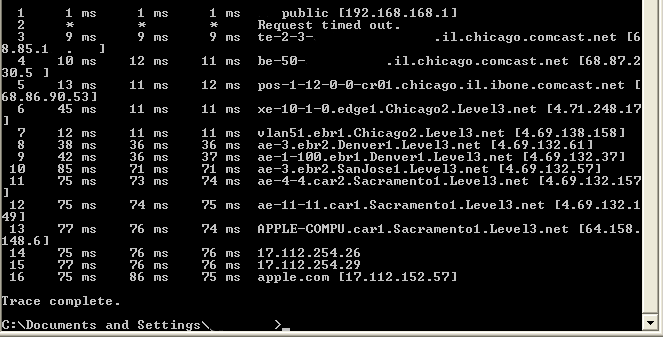
As you can see, my ping goes through the following:
A computer at 192.168.168.151 - My computer
A router at 192.168.168.1 - Local
A router at 68.85.1x.x - neighborhood
A router at 68.87.230.5x - Central Office
A router at 68.86.90.53 - Chicago backbone provider
A router at 4.71.248.17 - Chicago backbone provider
A router at 4.69.138.158 - Denver backbone provider
A router at 4.69.132.57 - San Jose backbone provider
A router at 4.69.132.157 - Sacramento backbone provider
A router at 4.69.132.149 - Sacramento backbone provider
A router at 64.158.148.6 - Apple Sacramento backbone provider
A router at 17.112.254.26 - Apple router
A router at 17.112.254.29 - Apple router
A webserver at 17.112.152.57 - Apple.com
That’s 12 routers just to get to apple.com. Impressive.
You’ll see that there are 12 different networks connected via a series of routers. None of this would be possible without these routers.
How does this all work?
MAC addresses, route tables, and a lot of configuration. Without getting too advanced (Keep It Simple Stupid KISS):
A switch will “remember” what port each MAC address is from. If the switch doesn’t know a MAC address source, it will write the MAC address and port number to it’s memory for future reference. If a switch doesn’t know the MAC destination, however, it will flood every port with the data. If no network responds, the switch simply throws out the packets of data.
A router will “remember” what port each MAC address is from. Remember that MAC addresses are physical addresses at the Layer 2. IP addresses are at Layer 3, so a conversion takes place:
Computers A and B are connected to a Switch. Computer A (192.168.1.2, MAC of 00-00-00-00-00-01) wants to send information to Computer B (192.168.1.3, MAC of 00-00-00-00-00-02). Computer A sends the packet to “192.168.1.3”. The switch looks in it’s table for that IP address. If it finds the IP, it then grabs the associated MAC address and finds what port that MAC is connected to. It then sends the data out that port. If the switch does NOT find the IP, it will send out the data to each port on the switch except the port it came from. If it gets a response, it will record the MAC address and port from the respondee. In our case, it’s computer B with 00-00-00-00-00-02.
What’s the difference between a router, a switch, and a hub?
A router routes, a switch switches, and a hub… well a hub just kinda sits there. Technically speaking, a Router will connect networks together, a switch will allow different network devices to communicate on the same network, and a hub extends the physical network. A hub is shared networking – if you have a 10/100 hub with 8 ports, each of the ports will share the total bandwidth of 100Mb. Hubs are half-duplex and are referred to as “dumb”. Switches are full-duplex and each port gets the entire bandwidth allotment. Many home routers also include a switch. A common example is a Linksys wireless router – it will include a WAN port, 5 LAN ports, and a pair of antennas.
So what about this layer 3 stuff?
The most common layer 3 protocols are TCP and UDP. While both protocols are basically the same in terms of the header/source/destination, they differ greatly in terms of usage. TCP is used when data integrity is required. Each packet of data is numbered and acknowledged. If a packet is “missing”, the computer will resend the same packet to the destination. UDP, on the other hand, has no integrity check. If a packet is received out of order it is discarded by the destination. Why would you want to discard out of order packets and not have the sender resend them? IP Phones, streaming video, streaming audio. Can you imagine talking on the phone and having parts of your conversation show up later? UDP is great for Live events – events where a delay is not accepted. TCP is used when integrity is required – grabbing email, downloading files, etc.
How about this “private” and “public” IP stuff?
Private IP addresses are those that can not be routed through the internet. Although technically you can use a “private range” of 17.112.152.x with a subnet of 255.255.255.0 on your home router, you would not be able to visit any apple websites. So, to keep things easier for everyone, the most common Private IPs are: 192.168.x.x, 172.16.x.x-172.31.x.x, and 10.x.x.x.
How is that different from your public IP? Most home users have a single Public IP, and usually it’s not statically assigned (meaning it can and will change if you ever lose your internet connection). Visit http://whatismyip.com sometime and see what your public IP address really is. We’ll assume that your private IP is 192.168.1.2 and your public IP is 17.112.152.57. A simple host lookup on the public IP will yield apple.com. If you were to ping apple.com, you will receive a response from the public IP (still 17.112.152.57). How can the two IP addresses be different? Because you have a router!
If you have a home network with 4 computers connected (2 laptops, a desktop, and an Xbox360), each has their own private IP (192.168.1.2, 192.168.1.3, 192.168.1.4, and 192.168.1.5 respectively), but they all share your public IP of 17.112.152.57. There is a process known as NAT that allows each of these devices to share a single public IP address. Every request sent outward to the internet gets modified by the router to have a unique source port. That way when the data comes back the unique source-turned-destination port will allow the router to “remember” which system requested the data. So if you’re browsing the web on your laptop while downloading updates on the xbox, there should be no conflicts of data.
Ports? What’s port 443?
Common ports are easy to find out. When you send for information from a website, it will run under port 80. If you want to request from a secure website, it will run under port 443. Common ones:
21 FTP
23 telnet
25 SMTP
53 DNS
80 HTTP
110 POP3
443 HTTPS
Your router will request the page on your behalf, sending the request to port 80 at apple.com. But it will inject port 57803 (random port number) as the source. When apple.com replies, the source is port 80 and their destination is your router at port 57803. The router then knows that you were requesting the information and forwards it onto you. Obviously this is done much more rapidly than I can type or you can read.
Hopefully that helps a little bit with the understanding of IPs and networking. I’ve only touched the surface when it comes to explaining all of this. And since I’m more of a visual learner, I’ll probably draw some pictures eventually.